
Affordable SMB Cybersecurity Technology for Comprehensive Coverage
Achieving Defense in Depth is possible for any size organization.
Sorting through cyber risk reduction options and layers can be daunting, confusing, overwhelming, exciting, challenging.. in various portions, varying by person. It is never simple, and it’s always changing. It’s also a very exciting time to be in the field of cybersecurity, especially if you really love small businesses. Massive investments in R&D within a globally collaborative infosec industry have made new cyber security technology easier to deploy and use than ever before, especially for smaller networks. Free IT security policy and educational support from a multitude of government agencies is promoting cyberawareness growth across all industries, prompting security collaboration with partners, vendors, customers and others. In short, great cybersecurity solutions are now affordably available to organizations of all sizes. The fog is lifting.
What is Defense in Depth, and what does it look like for small to medium sized organizations?
Email. Web browsing. File transfers. Password attacks. Port scanning. These are just a few of the major attack vectors commonly used to infiltrate networks and steal data. You can’t adequately protect against all of these with a single layer of defense. Human actions are the leading source of breaches, and most often, the actions are unintentional. In addition to human errors, unpatched applications and insecure network architecture can leave holes in your coverage where criminals can breach your defenses and travel through your network, stealing data and disrupting business. All these factors must be considered in your cybersecurity defense plan.
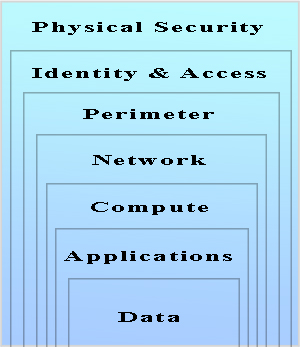
Defense in depth is an architecture of layers of coverage around your assets in order to slow and stop the advance of attacks through all these varied common attack vectors. If one line of defense is compromised, there are other coordinated defenses that identify and stop threats. By employing a blend of physical, logical, and managerial controls, and applying them to physical assets, network and compute resources, and human actions, you greatly reduce the chance of successful breaches. Further, if your perimeter is breached, defense in depth significantly increases the chances of arresting any network infiltration before your data is accessed by cyber criminals.
Technical Controls for SMB Cybersecurity
For small businesses, small enterprises and local governmental organizations, the most effective technical defense is usually a unified threat management system from a single vendor. While there are several options available on the market, most often we recommend the Fortinet Security Fabric for cost, ease of use, and growth potential. The Fortinet Next Generation Firewall (NGFW) can be deployed both on premises and in the cloud, with entry level units starting at around $1,200 for the first year. This basic entry level price includes hardware, software as a service with multiple daily updates to consistently address emerging threats, and a support contract with Fortinet. We assist our clients with deployments and set up as well. For on premises systems, the hardware cost is realized in the first year, so annual cost in subsequent years is lower, with additional discounting available for 3 and 5 year service and SaaS commitments.
We don’t just like the Fortigate because they have the most competitive pricing. They also deliver when it comes to speed and security excellence. Gartner has listed the Fortigate as the top NGFW for the most recent three years. Because the Fortigate has the largest market share for NGFW service, protecting both enterprises and governmental networks, they have the greatest data set to evaluate for identifying emerging threats. With consistent increases in research and development, they have been able to architect and offer the best next generation firewall solution on the market, and at the best price. Small businesses can get the same quality and level of coverage provided to and built for the world’s largest enterprises.
Fortinet does have a bit of a lagging reputation for poor customer service, but their customer service is maturing as well. If there ever is an issue, we are always happy to assist our clients with any customer service issues through our Fortinet partnership portal.
Businesses are attractive targets for hackers and weak security can lead to devastation. Learn how to get the complete protection your business needs – without having to sacrifice growth or performance. By investing in the right networking and security tools, small-medium sized businesses can significantly reduce their risk using the technologies that are designed to work together, offer strong protection, and are easy to use and manage.
Connect:
Have questions? Let’s talk! Please tell us a little bit about your organization and any known cybersecurity issues so we can best pair you with one of our professional analysts. We’ll get back to you within 48 hours. We offer free 30 minute consultations and we’re happy to answer questions and provide recommendations for next best steps for reaching your cybersecurity goals. You’re also welcome to call to schedule a consultation.
Technical Controls for SMB Cybersecurity
For small businesses, small enterprises and local governmental organizations, the most effective technical defense is usually a unified threat management system from a single vendor. While there are several options available on the market, most often we recommend the Fortinet Security Fabric for cost, ease of use, and growth potential. The Fortinet Next Generation Firewall (NGFW) can be deployed both on premises and in the cloud, with entry level units starting at around $1,200 for the first year. This basic entry level price includes hardware, software as a service with multiple daily updates to consistently address emerging threats, and a support contract with Fortinet. We assist our clients with deployments and set up as well. For on premises systems, the hardware cost is realized in the first year, so annual cost in subsequent years is lower, with additional discounting available for 3 and 5 year service and SaaS commitments.
We don’t just like the Fortigate because they have the most competitive pricing. They also deliver when it comes to speed and security excellence. Gartner has listed the Fortigate as the top NGFW for the most recent three years. Because the Fortigate has the largest market share for NGFW service, protecting both enterprises and governmental networks, they have the greatest data set to evaluate for identifying emerging threats. With consistent increases in research and development, they have been able to architect and offer the best next generation firewall solution on the market, and at the best price. Small businesses can get the same quality and level of coverage provided to and built for the world’s largest enterprises.
Fortinet does have a bit of a lagging reputation for poor customer service, but their customer service is maturing as well. If there ever is an issue, we are always happy to assist our clients with any customer service issues through our Fortinet partnership portal.
Businesses are attractive targets for hackers and weak security can lead to devastation. Learn how to get the complete protection your business needs – without having to sacrifice growth or performance. By investing in the right networking and security tools, small-medium sized businesses can significantly reduce their risk using the technologies that are designed to work together, offer strong protection, and are easy to use and manage.
Physical Controls for SMB Cyber Safety
Physical controls are perhaps the most straightforward and traditional measures of asset protection. Just as you protect your physical assets with locks and security systems, the physical servers where your data is stored need to be protected. This applies to all kinds of data storage however. Where ever your data is stored on premises, whether it be in local hard drives and file servers or on paper in physical files, protected data, when breached, opens potential back doors into your network resources. Malicious insider threats can are also a risk for data theft of sensitive and valuable information that is left unsecured. Cloud Data Storage security is also vitally important to your cybersecurity. But, let’s address on prem and cloud storage more specifically.
Physical Data Security On Premises
Defense in Depth Layers
Locking closets and racks for your servers are essential for on premises data storage. Monitored security systems have been fairly standard for decades, but now with IoT, security cameras and door access systems are now networked, helping to provide the necessary greater security for the modern threat landscape. (We address securely networking your on-site cameras and door locks in greater depth here.) In addition to on premises and server closet security, clean desktop policies should require all documents containing protected data be returned to locked cabinets at the close of the workday and that sensitive documents are not left out unattended at any time. Cable lock hardware can be used to further secure laptops, table top and tower computers during off hours.
The other consideration for on premises data security is not based in protecting your assets from bad actors, but is focused on natural disasters and other non-human caused events. It is wise to always have off-site backups of your onsite informational assets. When it comes to business continuity, whether your well encrypted data was stolen by a ransomware attacker or was destroyed by a hurricane, if you irretrievably lose your data, you may never recover. Alternative site backups can bring you back from total losses and keep you operational.
Physical Security of your Data in the Cloud
Additionally, you need to ensure that wherever your data is stored in the cloud has adequate physical security. This responsibility falls to the provider of the cloud services, but it is imperative to read the fine print on your service agreements to ensure that the cloud provider has robust mechanisms in place to prevent security breaches.
For data held in the cloud, it is generally the responsibility of the cloud provider to physically secure the servers holding data. Keep an inventory of your cloud service providers, and be sure to read the service agreements to confirm their responsibility for physical security.

